Your donation will support the student journalists of West High School. Your contribution will allow us to purchase Scholarship Yearbooks, newsroom equipment and cover our annual website hosting costs.
The issue of internet security
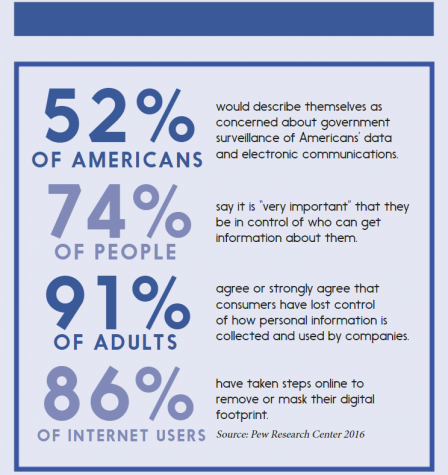
Amid Internet security scandals, the world learned that there are far less protections for what is put on the web or picked up by new technological devices than people believe. No matter the effort, what’s put on the Internet can never truly disappear for good
December 17, 2018
From Facebook leaking user data to the Russia investigation, technology scandals have catapulted into the spotlight, raising questions about data security and privacy. As accessibility to technology becomes increasingly available, the problem only becomes more personal.One of the most common ways that user data is exploited is through targeted advertising, where companies track web activity and create ads promoting specific products or services tailored to that person’s interests. This has incited controversy, as the boundaries regarding the legality of privacy invasion are uncertain.
“While I don’t think that laws and courts have been completely clear on [targeted advertising], that type of data use is not illegal and is in fact Google’s, Facebook’s and the Des Moines Register’s primary business model,” said ICCSD Director of Technology Adam Kurth. “Whether this type of data collection is problematic or nefarious is in the eye of the beholder; some people feel that their privacy has been violated, while others don’t give it a second thought.”
However, data collection is no longer limited to only targeted advertising. For example, smart-home devices such as the Amazon Alexa and Google Home are now able to listen in on conversations without the user’s knowledge.
“I was recently at a friend’s house who has an Alexa. We were talking about a particular Amazon product at night while having dinner. The next day, those products were on his Facebook feed and he got an email saying they found something he might be interested in,” said Dale Felton, Senior Information Security Analyst at ACT. “I heard someone say it best when they said, ‘Why would we pay a lot of money for devices that are constantly listening?’”
Another method of data collection that has grown more controversial in terms of privacy is camera spying, where someone can watch what’s going on through a camera in anyone’s device without the user’s knowledge.
Molly Erickson ’18, a student in the Chromebook IT Department, has seen this firsthand. She has noticed that every Chromebook she has repaired has a piece of tape over the camera.
“Literally everyone does it because people are paranoid about it, and it’s justified. I like being secure, and I like feeling safe,” Erickson said.
While the concern over data security has grown, so has the necessity to find a balance between user convenience and privacy.
Erickson believes that among her peers, the issue has become too normalized for any attention to come to it.
“I feel like if you’re using technology, it’s kind of expected that something’s going to happen,” Erickson said. “Not everything can be so secure, so [people] might as well be okay with that. I don’t think anyone cares enough because so many [companies] do it that you can’t end it.”
Felton agrees that the “out of sight, out of mind” ideology has been ingrained not only among everyday citizens, but businesses as well. Having previously worked in the banking IT industry, Felton has also noticed that banks would buy cheaper less secure devices rather than more secure and expensive devices.
“You see people all the time in airports and coffee shops accessing their bank accounts or other very private data. Generally in a public area, the user is not protected and with a few simple programs, someone could be on their device capturing data,” Felton said. “It’s definitely more convenient to turn a blind eye to this instead of using a firewall at home or properly setting complex passwords.”
Currently, students in the ICCSD District have data being collected through school-monitored services, such as Canvas and Securly. Securly is the content-filtering service on Chromebooks that monitors all student web activity and gives both the school district and parents the availability to control students’ web activity. However, this data is not currently used by the district.
“Student email addresses and website visits are collected as part of the primary function of the system … but ICCSD does not use this data proactively. We will pull internet access data at the request of the school administrators, but this does not occur on a regular basis,” Kurth said. “It is worth noting that all companies with whom we share student data are required to be in compliance with FERPA and COPPA laws that protect students’ educational records and online safety. Furthermore, the companies cannot use student data for advertising purposes and cannot sell student data for any purpose.”
Student data is also held within the ACT headquarters located in Iowa City. While this data is heavily protected, Felton has noted that hacking attempts are frequent.
“There is a very small group of ACT employees that have access to that data. In order to get this access, [employees need] to have approval from very upper management,” Felton said. “We see hacking attempts every single day. We have policies and controls in place to make sure the ‘bad actors’ stay out. Between audits, penetration tests conducted by an outside company, well trained staff and some of the latest tech, we make sure data is only available to those who need it. As long as I’ve been with ACT, I have not heard of a single student data breach.”
Nevertheless, as technology continues to advance, many have made comparisons to George Orwell’s 1984.
“It’s a really scary prediction when you read [1984] and the more you think about it, it’s less of a prediction and more of our reality because everywhere you look there are security cameras, screens, and companies can target you ads,” Erickson said. “The government also has watch lists and can track your information online and all that’s there.”
Many have questioned whether the issue stems from the technology user or other parties and who should be responsible for resolving the problem, as both topics of discussion have been under constant deliberation.
“I think it’s a little of both because … when was the last time someone actually read the terms and conditions? Then also the fact that there isn’t really any government regulation over this issue, and they haven’t done too much about it,” Erickson said. “I really think that people should be more aware of what’s happening with their data and unless we take precautions and be more educated about it, things are going to get worse.”
Many also believe that the government needs to assume more responsibility in the regulation and evaluation of data and security.
“I believe that eventually, the Bill of Rights does need to be reevaluated. The First Amendment was written Dec. 15, 1791. That was about 226 years go. Based on how much tech has changed and how fast it’s growing, how can a bill written 226 years ago still be one-hundred percent relevant?” Felton said.
Kurth agrees, believing both sides need to be committed to change.
“It’s the role of the lawmakers, the courts and members of the public to establish firm rules with regard to vulnerabilities to ensure the maintenance of a free, democratic society,” Kurth said.